Emails serve as a common entry point for malware. Thanks to deceptive tactics, cybercriminals can trick users into downloading malicious software, which can lead to data theft, financial loss, and other serious consequences. This is why it is vital to know how to identify malware hidden in emails. Check these five methods that will help you and your organization avoid falling victim to a malware infection.
1. Check for Suspicious Links
Contents
Criminals often distribute malware via links that lead to websites requiring you to download malicious files. Before you click on any link, make sure to move your mouse over the link without clicking. This will show you the web address (URL). If the URL looks strange or does not match the link in the email, do not click on it.
Sometimes, bad actors use legitimate websites to host their malicious files. These usually include file-sharing platforms like Dropbox. In this case, it is always best to use a free tool like the ANY.RUN sandbox.
This cloud service lets you open the link in a safe, virtual space and see if it poses a risk. It also automatically finds threats and alerts you with a “Malicious activity” label. This way, you can check suspicious links without risking your device or data.
Check out this ANY.RUN sandbox analysis of a phishing link.
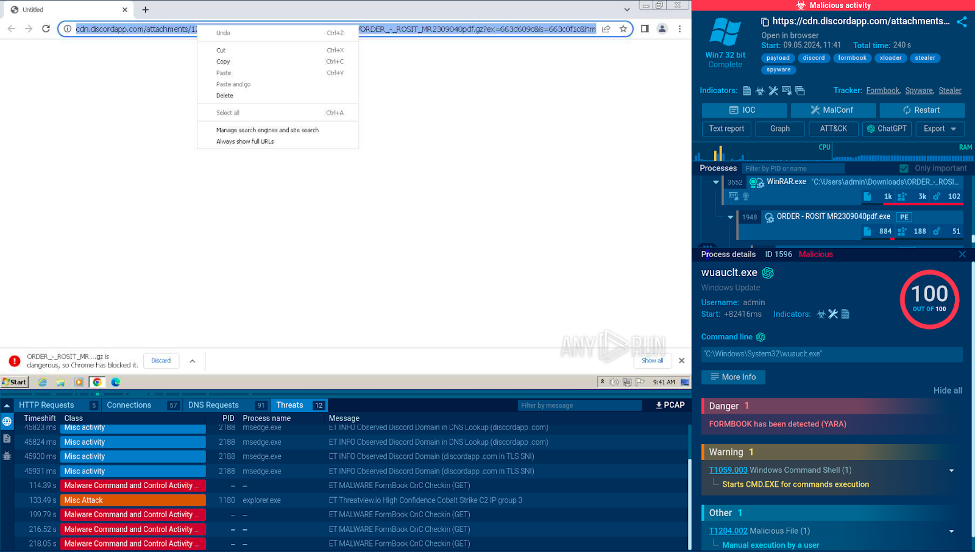
Analysis of a phishing URL in ANY.RUN
After opening the URL in a browser inside the sandbox, we can see how it automatically downloads an archive. In the archive, we find an executable file. Once we launch it, the sandbox immediately detects the Formbook malware, a widespread trojan that steals sensitive data from infected systems.
2. Be Cautious with Email Attachments
Email attachments are another common vector of attack. Be on the lookout for unexpected or unsolicited attachments, especially those that are executable files (.exe, .bat, .msi). These file types can automatically run a malware program when launched.
To avoid detection by antivirus software, threat actors often place executable files in archives (.zip, .rar) and protect them with a password, which is then sent as part of the email. In such cases, you must be very cautious and avoid running the files on your machine.
Instead, you can once again use the ANY.RUN sandbox to safely explore any attachment in your email.
Consider this example of a file named “COMPLAINT.pdf.exe”.
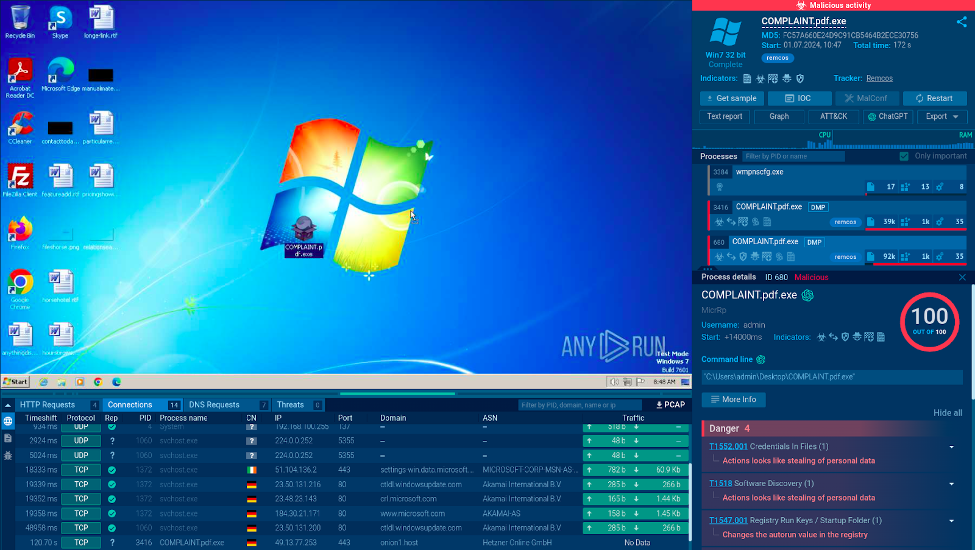
The “COMPLAINT.pdf.exe” file in ANY.RUN
Here, we can observe another common technique used by criminals. They can attempt to disguise the executable by placing a fake extension in front of the actual one. In this case, it is the .pdf extension. The name of the file is also intentionally meant to trick the victim into opening it.
By safely executing this file in the sandbox, we get to see that it is actually the Remcos malware, a trojan that allows attackers to maintain a remote control over the infected device.
3. Look for Grammatical and Spelling Errors
Legitimate organizations typically ensure their emails are free from grammatical errors and spelling mistakes. If an email is filled with such errors, it could be a sign that it’s a phishing attempt. Cybercriminals often rely on the urgency and fear they create in their messages to prevent recipients from noticing these errors.
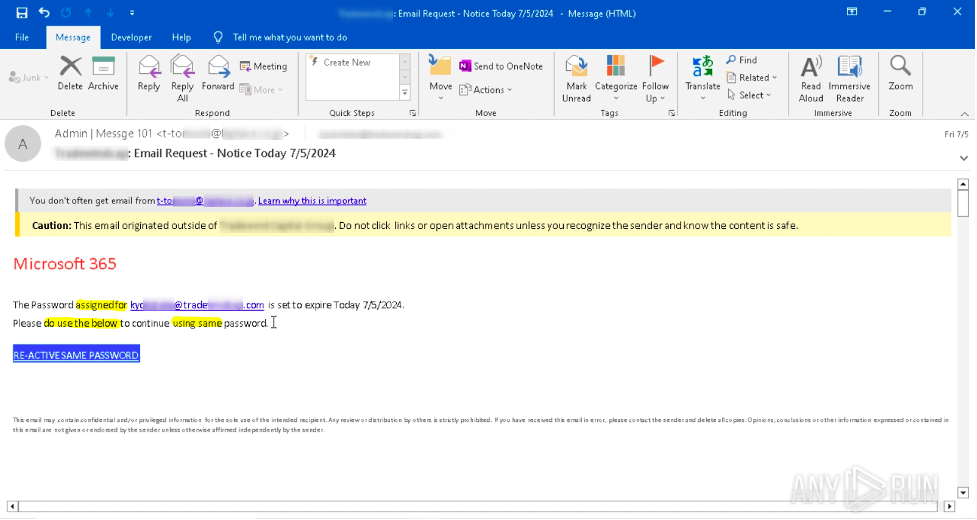
A phishing email with mistakes
Consider the example above of a phishing email analyzed in ANY.RUN. The text of the message contains obvious mistakes, including omitted articles, spaces, and entire words, as well as incorrect use of words (e.g. “Re-active” instead of “reactivate”).
4. Beware of Email Spoofing
Email spoofing is a tactic where cybercriminals impersonate a trusted sender to trick you into opening a malicious email. They can mimic the email address, logo, and style of legitimate organizations.
To detect spoofed emails, look for inconsistencies in the sender’s email address, unusual language, or requests for sensitive information.
Still, sometimes legitimate senders can be compromised. This is why it is crucial to look at other aspects of the email to determine its safety.
5. Use a Spam Filtering System
Another effective way to detect emails that may contain malware is by using a spam filtering system. These tools can automatically detect and filter out potentially harmful emails, reducing the risk of malware reaching your inbox.
ANY.RUN incorporates the open-source Rspamd module that uses a variety of techniques to detect spam and malware. Rspamd provides a score that reflects the reputation of the analyzed email. If this score is above 20, the email is likely to be originating from a threat actor.
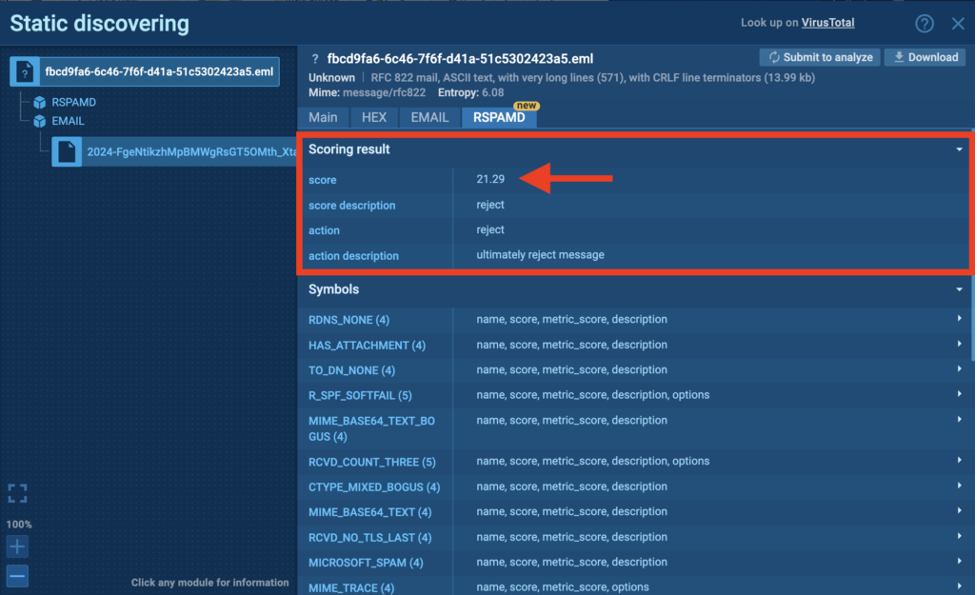
Rspamd analysis in ANY.RUN
The image above shows how the score works in ANY.RUN. All you need to do is upload your email to the sandbox and the Rspamd module will provide you with a conclusive result.
Conclusion
Detecting malware in your email requires vigilance, caution, and effective tools like ANY.RUN. By following these guidelines, you will significantly reduce your risk of suffering from a malware attack.


