Despite the fact that Google, owner of GMail, tries to strengthen its security by using physical keys or dual authentication, with nearly 2 billion users worldwide, GMail will still be the most hacked mailbox.
The GMail service is more than just email. Today, having a Google account includes everything that can be done on the Internet such as messaging, videos, images, discussions, calendar, forums, site listings… It can be very annoying to lose control of your GMail account because your entire digital life can be put in the wrong hands.
We can do everything with a GMail account, by using an account chips there is no need to register on websites when you want purchases items, a single click associates the account with the website.
This article aims to prevent and warn about the dangers of hackers. They use flaws that must be known in order to avoid having his GMail account hacked.
Method 1: PASS BREAKER
PASS BREAKER is the software specially designed to decrypt GMail account passwords from an email. It was designed in partnership with hackers specializing in account recovery. PASS BREAKER can be used by anyone because it works on smartphone, tablet and computer.
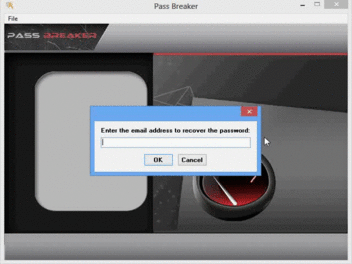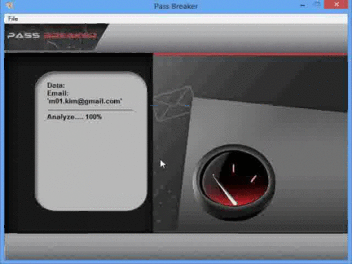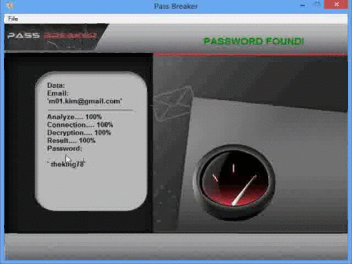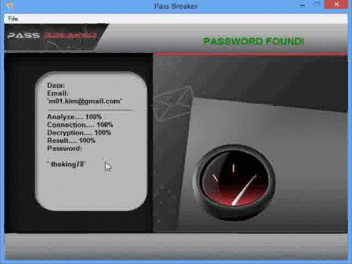
Its use is very simple, the user enters an email then PASS BREAKER will automatically decode it and display the password GMail on its screen. How does it work ? It will connect to the protected data storage and make the balance between the email you entered and the password associated with it.
Here is the demonstation:
From this software you can find any GMail account password without limites and thus connect to it.
You can download it from here: https://www.passwordrevelator.net/en/passbreaker.php
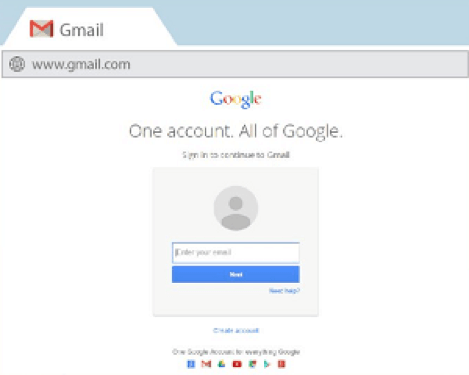
Method 2: Divert the GMail login URL
When a victim is connected to an Internet network with many other people on the same network, there is a good chance that a hacker drags malicious code into it and hack a GMail account.
Indeed, when you go to the link to read your emails https://mail.google.com/mail/?tab=wm, a malicious hacker could very well intercept this url and set the router for that it redirects you to a phishing site. You will not notice it! Indeed, you will have correctly clicked on the connection link to mailboxes from the official Google website and you will be redirected to a fake login page.
This is a technique of Domain Name System Hijacking or DNS Hijacking, this hack is normaly used by IT professionals hackers. On the browser you will be properly connected to your mail as in the URL you will see that you are on the right page, but in reality, you will be on a clone site created especially by the hacker. There is no way for you to detect this hacking attempt and no way to protect yourself.
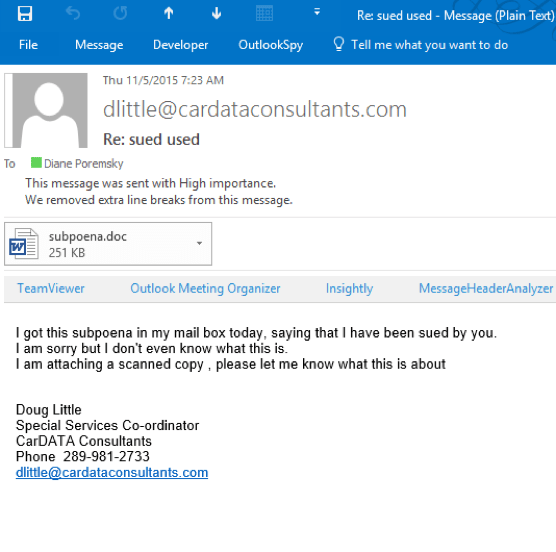
Method 3 : Send an attachment in an email
It happens to receive emails containing attachments like PowerPoint or .doc extensions, it can come from family or colleagues but also from hackers. These documents seem trivial but by looking at them more closely, they are malware hidden inside for the sole purpose of hacking your equipment.
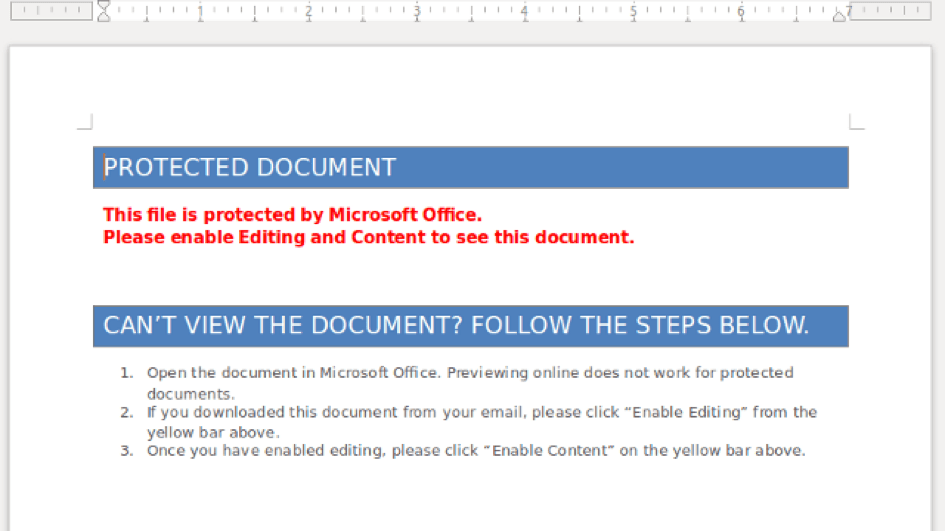
These documents have lines of code that, once launched, will go on the Internet to download a malicious program and install it. To force your hand and gain confidence, he sends you emails explaining that you have placed an order or that you will receive money. Once you open the attachment, an image appears to allow you to open and read the text.
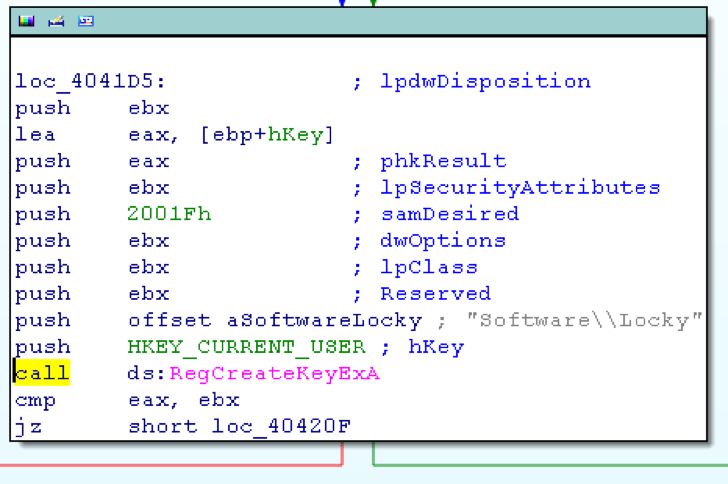
The code is in basic programmed and as you can see here, it is clear that it wants to download then run a virus:
He will then ask you for a ransom or hack your email and password.